-
Notifications
You must be signed in to change notification settings - Fork 17.9k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
cmd/go: cryptic error message when git repository is reachable locally but not reachable from sum.golang.org google SaaS server #51174
Comments
name resolution wild goose chase / red herringNow I'm going to attempt to figure out WHY this happens. First of all it looks like it might start here: go/src/cmd/go/internal/vcs/vcs.go Lines 943 to 955 in faa0409
which goes go/src/cmd/go/internal/web/api.go Lines 166 to 183 in faa0409
then go/src/cmd/go/internal/web/http.go Line 63 in faa0409
then go/src/cmd/go/internal/web/http.go Lines 122 to 127 in faa0409
then go/src/cmd/go/internal/web/http.go Lines 91 to 115 in faa0409
then it calls go/src/cmd/go/internal/web/http.go Lines 44 to 61 in faa0409
I'm assuming since the transport isn't specified on the Lines 38 to 54 in faa0409
At this point I have no idea why the bug is happening and I feel like I would have to learn how to run an interactive debugger against |
name resolution wild goose chase / red herringhttps://paste.cyberia.club/~forest/409095b1a74946eb6ec0a9dbbe421f517411a1c5
https://paste.cyberia.club/~forest/671d55f02c152fda743368052958023f20acbdcf
https://paste.cyberia.club/~forest/52340c2560865d0015cfcbe9e62f84647f76ea74
https://paste.cyberia.club/~forest/b49fa1f36214ad9f11ac3a92ccc0769079710dd1
https://paste.cyberia.club/~forest/ee822db61399c9505d323ba21d3e24cb787f7916
Conclusions I have drawn from my
For some reason, the This caused the following condition to fall through:
so I decided to figure out why But first, I decided to debug my sample program and figure out what it was doing differently. More on that later. Finally, I got to the part where the go code stops and it calls libc or makes a syscall or whatever: Where I can see the wrong (not from the hosts file) address |
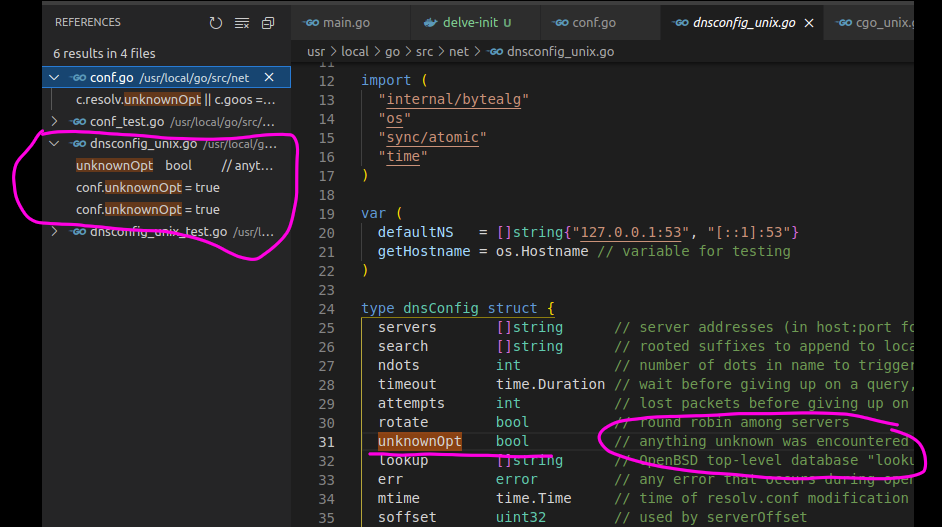
name resolution wild goose chase / red herringunknownOpt is being caused by the line |
name resolution wild goose chase / red herringhttps://www.man7.org/linux/man-pages/man5/resolv.conf.5.html |
name resolution wild goose chase / red herringOk. So it sounds like this is happening because go does not support these `resolv.conf` options, so it's throwing up its hands and falling back to something which doesn't work... ? is that right ? But that doesn't explain why example app with |
|
Wait hang on i got confused, hold the phone,
but i'm still seeing |
|
OK, so whatever I was looking at before appears to not be related to the actual problem. however if i change my breakpoint condition to So where the hell is it getting |
|
OMFG its happening because of a google service that is trying to connect to my git server . The error I am seeing is being thrown on the google telemetry server.
See the explanation at https://sum.golang.org The google telemetry built into the |
|
OK, to summarize:
|
go get seems to ignore /etc/hosts (Ubuntu, nsswitch.conf exists) |
I'm getting big
vibes right now, not gonna lie. |
|
The work around is written here https://medium.com/mabar/today-i-learned-fix-go-get-private-repository-return-error-reading-sum-golang-org-lookup-93058a058dd8 The error message should explain this workaround. Also yall should probably not make tools that run on our work stations (like |
|
See https://go.dev/ref/mod#private-module-proxy-direct |
|
This is why I use the word "misleading", because pretty much every golang developer I run into (including myself before this issue thread) has no idea that this feature exists, and thier mental model of what So, in terms of my lived experience working with go for several years and seeing other people doing the same, I know that it is in fact misleading. Whether it talks about this in some manual page somewhere or not doesn't really matter; no one is going to read that until after they discover that |
|
I think the fix here is to modify |

What version of Go are you using (
go version)?Does this issue reproduce with the latest release?
Yes
What operating system and processor architecture are you using (
go env)?go envOutputWhat did you do?
I am trying to
go geta module while I'm developing an app to fix my DNS issues, howevergo getis ignoring the hosts file entry I created to temporarily fix my git server's incorrect domain name.does not work because my git server git.sequentialread.com is not reachable from the sum.golang.org google SaaS server which is tightly integrated into the way thego getcommand works.What did you expect to see?
I expected the
go getsoftware do what I asked, go to my git server and download the module.However, in the event that
go getcannot do that for me, I expected thego getsoftware to tell me in clear, human-readable terms why it cannot do that.What did you see instead?
When I 1st saw this error, I was 100% convinced that it was an issue related to golang not parsing
/etc/resolv.conf,/etc/nsswitch.confor/etc/hostscorrectly. I quickly realized that it only happened withgo get, not with a normal http call to git.sequentialread.com, so I decided to investigate further. However, after following that red herring all day long, I finally got to the point where I had run out of things to check and I could not make sense of what I was seeing, according to delvego getWAS resolving the right IP address71.34.5.123not the wrong one71.34.16.185. It was connecting to71.34.5.123, not71.34.16.185. But I was still seeing an error that saysdial tcp 71.34.16.185:443: connect: connection refusedEventually with dumb luck / trying anything after running out of options, I found the answer:
forest@thingpad:~$ curl https://sum.golang.org/lookup/git.sequentialread.com/forest/config-lite@v0.0.0-20220122212408-4941a7aa3dc0not found: git.sequentialread.com/forest/config-lite@v0.0.0-20220122212408-4941a7aa3dc0: unrecognized import path "git.sequentialread.com/forest/config-lite": https fetch: Get "https://git.sequentialread.com/forest/config-lite?go-get=1": dial tcp 71.34.16.185:443: connect: connection refusedThe error message I was seeing was actually being thrown on google's server, not on my computer.
The text was updated successfully, but these errors were encountered: