New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
testing: successive integer and boolean mutations can be the same #48291
Comments
Flip booleans when mutating rather than keeping the same value 50% of the time. Fixes part of golang#48291.
… mutating Flip booleans when mutating rather than keeping the same value 50% of the time. Fixes part of golang#48291.
|
With change #48292 I see a 25% reduction in work done by the fuzzer when the signature of the function under test is func(t *testing.T, b []byte, on bool) |
… mutating Flip booleans when mutating rather than keeping the same value 50% of the time. Updates golang#48291.
|
Change https://golang.org/cl/348849 mentions this issue: |
|
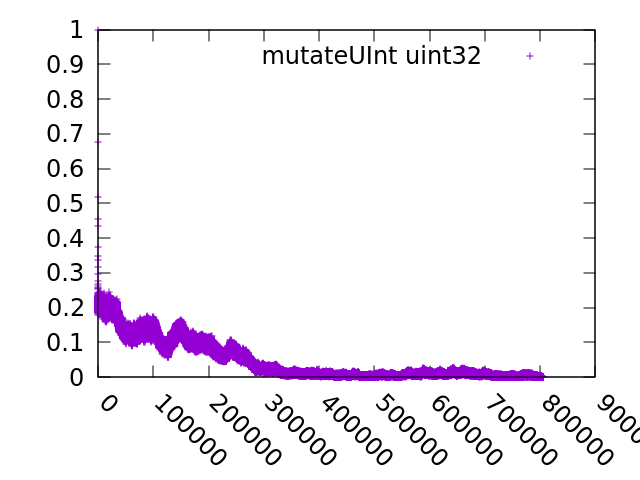
The int mutators are actually really interesting from a mathematical point of view. They are random walks with non-local conditions (the probability of a jump depends on the distance from the extreme points of the integer). This gives quite strange probability distributions. Here's what a sample of the distribution (starting a zero) looks like for uint8 (forgive the gnuplot purple): uin32 looks like a slow shuffle relatively close to zero but eventually it'd probably look something like uint8 The mutator is here: go/src/internal/fuzz/mutator.go Lines 165 to 197 in 7c648e2
Some properties of the mutator which are undesirable:
A more straight forward way to mutate an int would be to pick a random bit and flip it. That gives a uniform distribution of values, will never leave the integer unchanged and probably be good for things like flags. |
… mutating Flip booleans when mutating rather than keeping the same value 50% of the time. Updates golang#48291.
|
I think I just ran into this bug. I wrote a test function that panics if an input I found two workarounds that work for me:
See https://github.com/evanj/gofuzztesting for a reproduction |

What version of Go are you using (
go version)?Does this issue reproduce with the latest release?
n/a
What operating system and processor architecture are you using (
go env)?go envOutputWhat did you do?
Ran this fuzz test:
I have a bpftrace script:
Using that during runs of FuzzInt etc I can see that I get successive inputs to the fuzzer which are the same. For the boolean it's ~50% of the time, for uint8 about 0.3% and the rest 0.2%. I was taking a look because I had a test with this signature
and I'd see about 1/4 of the time it was executing the same test case as the previous run.
What did you expect to see?
I'd expect a mutation of a boolean to just flip the value true->false, false->true. There's no need for anything probabilistic here. For the ints, it's not as obvious of a problem but if my test signature was
the fuzzer would be doing the same work twice ~0.1% of the time. Not a massive amount but multiplied over all golang CIs, it's significant. My attempt at keeping CO2 in the ground 😅
What did you see instead?
Mutations which are no-ops.
The text was updated successfully, but these errors were encountered: