New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
proposal: spec: disallow Hangul filler codepoints in Go identifiers #40717
Comments
|
Apart from code golf, can these been used maliciously? |
|
@davecheney I see much potential for confusion in code review by hijacking names of basic types: Go playground: https://play.golang.org/p/EYIrCh9XtI_u func main() {
var v interface{}
fmt.Println(v)
v = interfaceᅟ{}
fmt.Println(v)
}
type interfaceᅟ struct{}Output: |
|
I'd hope that widespread use of this style of identifier would be self correcting via natural selection. Said another way, rather than changing the language, can this problem be solved by telling people that this isn't a good way to write code? |
|
Relevant issue about homographs attacks with go/vet: #20115 Seems this would be a similar use case. Referencing rsc in #20209 (comment)
|
Looks like you missed U+FFA0. But where in the Unicode standard does it say these are zero-width spaces? I do see that they (including U+FFA0) have the Default_Ignorable_Code_Point property, and they are the only Letter-classified code points that do. So we should probably include them in the vet checks being contemplated in #20115. Also, at least in the font I'm using, there's a clear indication that dodgy Unicode is happening: |
|
I suggest closing this as a duplicate of #20115. |
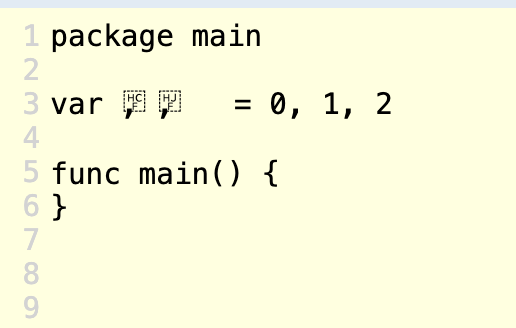
The Hangul filler codepoints (U+115F, U+1160, U+3164) are rendered as zero-width white space as specified by the Unicode standard. And they are allowed in Go identifiers.
https://twitter.com/omengue/status/1293476660268998656
They are only useful for obfuscation. Despites that would be a breaking change I propose to forbid them in Go 1 spec as I only see nasty uses.
What version of Go are you using (
go version)?Does this issue reproduce with the latest release?
yes
What did you do?
Go Playground: https://play.golang.org/p/bOmUvRfC3Co
What did you expect to see?
Compile time failure.
What did you see instead?
Compiles fine.
The text was updated successfully, but these errors were encountered: