New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
crypto/x509: SSL_CERT_DIR should support multiple directories separated by a colon like OpenSSL and BoringSSL do #35325
Comments
|
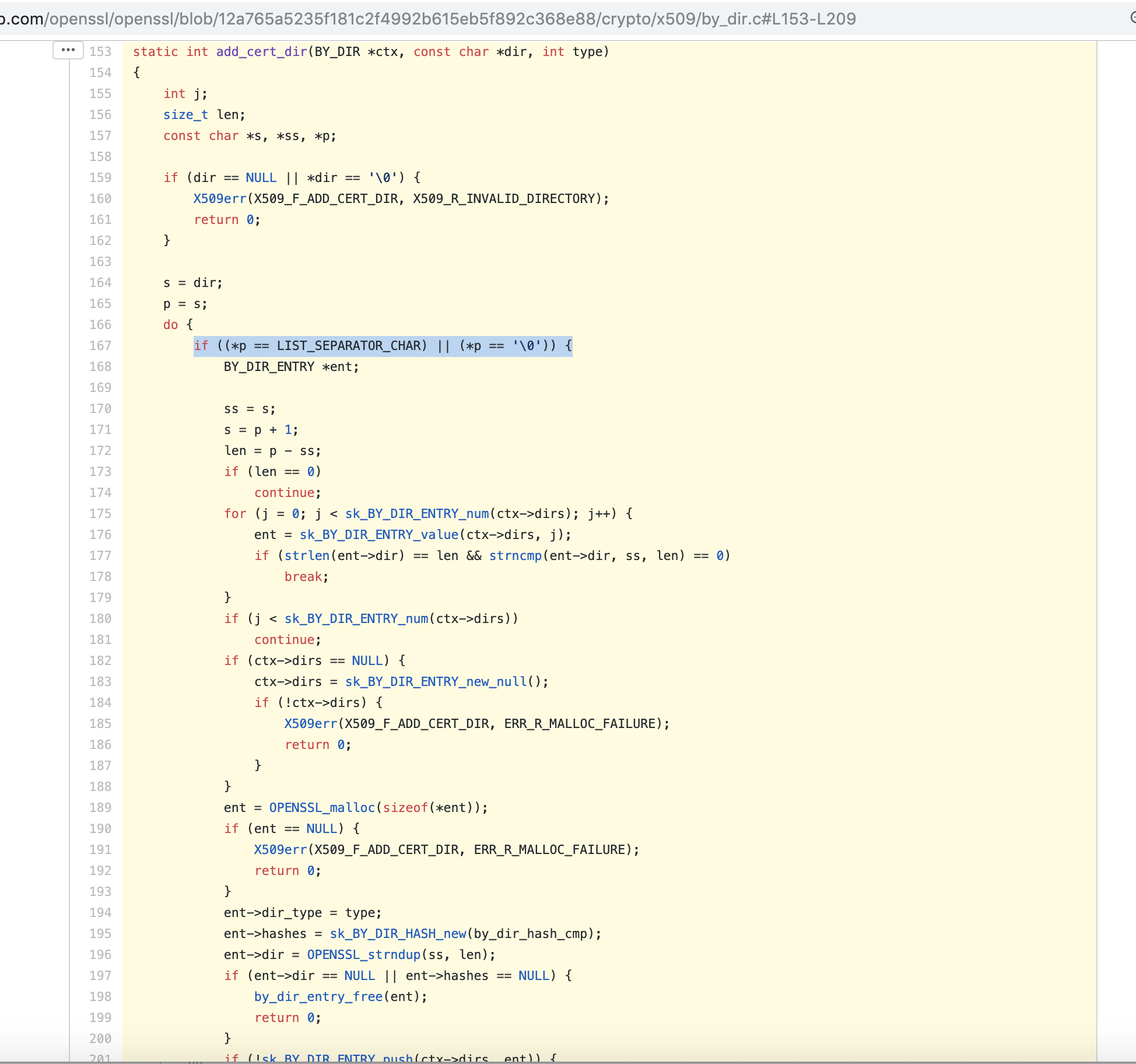
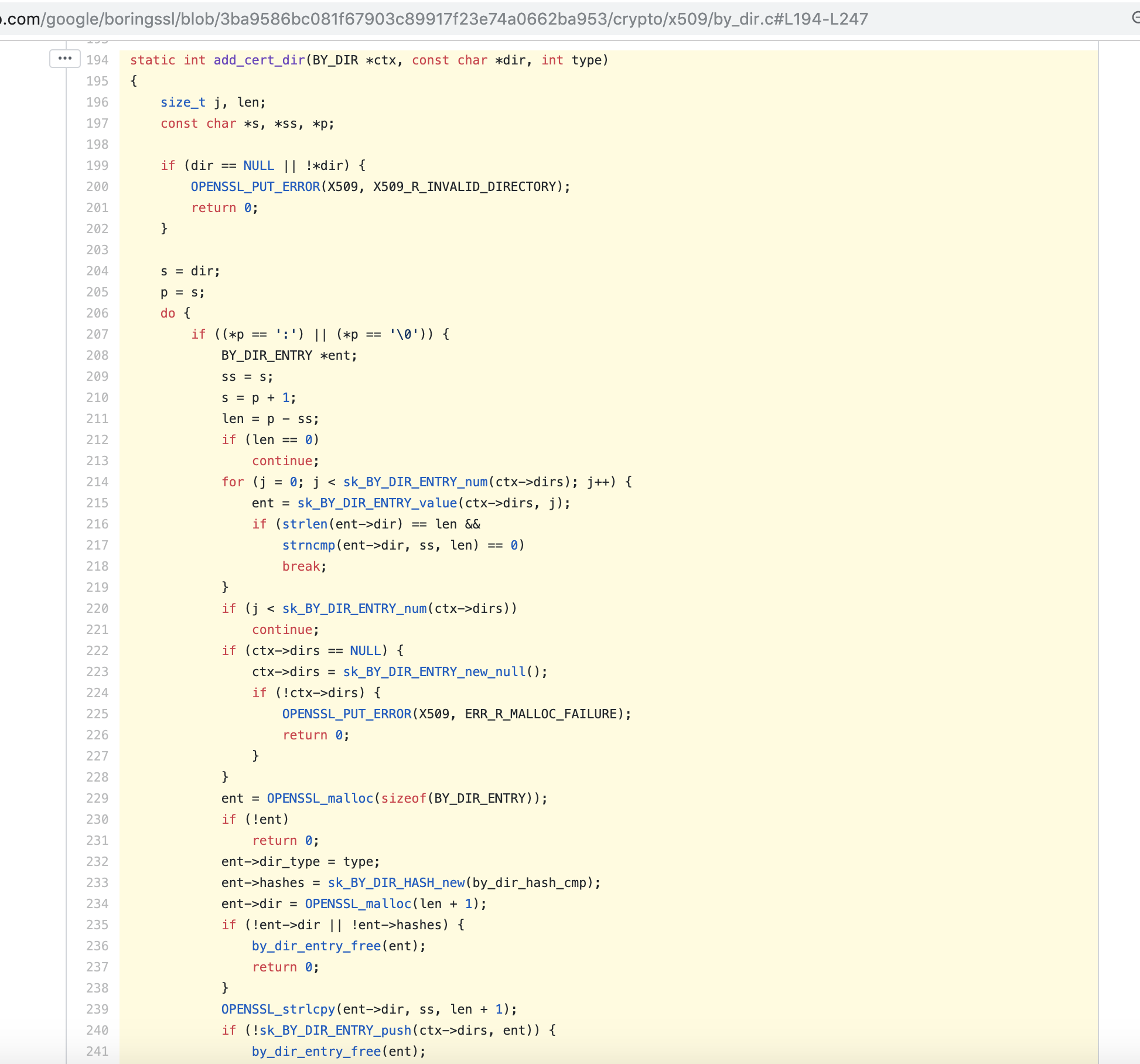
Thank you for filing this issue @freedge and welcome to the Go project! Great catch! You are right, OpenSSL and BoringSSL both recognize the colon separator as per OpenSSLhttps://github.com/openssl/openssl/blob/12a765a5235f181c2f4992b615eb5f892c368e88/crypto/x509/by_dir.c#L153-L209 BoringSSLhttps://github.com/google/boringssl/blob/3ba9586bc081f67903c89917f23e74a0662ba953/crypto/x509/by_dir.c#L194-L247 Proposed fixThe fix would seem pretty simple IMHO, we can change go/src/crypto/x509/root_unix.go Lines 60 to 62 in a8fc82f
to if d := os.Getenv(certDirEnv); d != "" {
// OpenSSL and BoringSSL both use ":" as the SSL_CERT_DIR separator.
// See:
// * https://golang.org/issue/35325
// * https://www.openssl.org/docs/man1.0.2/man1/c_rehash.html
dirs = strings.Split(d, ":")
} |
|
Change https://golang.org/cl/205237 mentions this issue: |
|
@freedge I sent a CL but we are currently in a code freeze, so this will have to wait until February 2020. |
|
super cool, thanks for your quick work!
I think having an InsecureSkipVerify option in the tls.Config (or a -k option to curl) is a mistake. The doc in tls.Config says it "should be used only for testing" but it does not describe any alternative, and there is nothing that validates that this parameter is not used on a production system. Practically, it is just too convenient to set up a simple boolean to make your stuff work (solving your immediate problem: connecting to a server, no matter its certificate), that people won't look for alternatives. This is what govc (cli to target the vmware api) does:
SSL_CERT_DIR is a pretty unknown environment variable. But if you think about having every single tool written in go getting rid of the InsecureSkipVerifyMode config parameter, while minimizing the development cost, and the burden put on the user, then SSL_CERT_DIR is a good choice. 0 development needed, and users can just put it into their environment (condition being: it does not break other tools! which can now be achieved thanks to your work) - much better than coding a tls-ca-certs parameter yourself, that users need to specify at every call. Next step could be to ease the retrieval of that certificate (eg: if certificate is untrusted, provide it into the Error message thrown by httpclient?) and cover extra usecases (for example certificate is for a subject that is different from the hostname in the URL)... To sum up, nobody complained because SSL_CERT_DIR is not well known and security not that important. In any case, thanks for your work, I'm just reporting it as it would save me 15 lines of code for my own little project - for which I am the only user :) |
What version of Go are you using (
go version)?Does this issue reproduce with the latest release?
yes
What operating system and processor architecture are you using (
go env)?go envOutputWhat did you do?
Set:
Then perform a call to a https service using http.Client.
This piece of code https://golang.org/src/crypto/x509/root_unix.go#L60
reads the SSL_CERT_DIR as a single path.
What did you expect to see?
as per doc from https://www.openssl.org/docs/man1.0.2/man1/c_rehash.html
This works for curl as well, and is convenient to provide some extract certificates on top of the default ones.
What did you see instead?
The text was updated successfully, but these errors were encountered: